| Welcome, Guest |
You have to register before you can post on our site.
|
|
|
|
Welcome Guest!
|
| Welcome to the Promo2day Community, where we feature software giveaways, computer discussion, along with a fun, safe atmosphere! If your reading this it means you are not yet registered.
You will need to Register before you can make posts, chat or enter the forum giveaways.
Be sure to also visit the Help/FAQ page.
|
| WinRAR v7 full review |
|
Posted by: Nicos18 - 03-10-2024 , 04:20 PM - Forum: Written Reviews
- Replies (3)
|
 |
WinRAR 7 Review
WinRAR is the official client to create RAR archives on Windows
RAR archives let compress even more some files that which other formats get a lesser compression and the unicity of RAR archives is the addition of an error recovery feature that helps in case some files are being corrupted. For this aspect, the RAR format is the best compression format to preserve integrity of important files. RAR files can compress contents about 30% more efficiently than a standard ZIP file.
These are the main features of WinRAR:
· Support for popular archive format (RAR, ZIP, ISO and many others)
· Easy-to-use GUI
· Splitting of archives, which makes easier to separate files if they are too big
· AES 256-bit encryption to make your data secure
· The ability to automatically select the best compression method for multimedia files
· Support for over 40 languages
· Drag-and-drop functionality
· Recovery record, to help you recover RAR archives in case of data corruption
· Perpetual license with no subscription and competitive pricing
· Option to create a self-extraction archive, also known as SFX
System requirements
WinRAR is compatible with Windows 11, 10, 8.1, 7 and Vista. There is also a free counterpart for Android phones (for Android 4.4.and above), and also a command-line version for Linux, FreeBSD, and MAC OS X. More information are in the “useful resources" section
Pricing:
WinRAR costs about 29$ for a 1-license, and (only if you want) you can add a maintenance option that costs only about 5$, which lets you have the latest WinRAR version for 1-year and, in addition, it offers the support if you lost your license key, receiving it in about 48 hours from the request. Lastly, you can also order a physical CD with the software, useful is you have a slow connection and want to have a physical backup copy of your purchased WinRAR.

win.rar GmbH released the final version of WinRAR 7 just few weeks ago that includes new features, improvements and bug fixes
Here are the new features of WinRAR 7:
· Enhance compression capabilities: support dictionary sizes up to 64GB allowing for best compression ratio
· New path length of 65365 characters, useful in cases of complex directory structures
· Improved security with the “Propagate Mark of the Web” option, which provides advanced control over security zone information for extracted files
· New advanced search algorithms, which enable WinRAR to locale longer and more distant repeated data blocks
· UI and settings enhancements, with a more friendly UI and more customization options
· Benchmarking improvements, allowing users to specify the number of threads and copy the results to the clipboard
· Other improvements and fixes, including a fix for a critical flaw
For a detailed changelog of WinRAR 7 and previous versions, please visit this link: https://www.win-rar.com/whatsnew.html
The installation of WinRAR is straightforward and easy to carry out:
1) Go to this link https://www.win-rar.com/download.html?&L=0
2) From this page, you can choose for the 32-bit and 64-bit version
3) Once downloaded, run or save the file and execute it
4) Accept the various Windows UACs
5) Select the destination folder and click install
6) Now you can choose which extensions associate with WinRAR and some other configurations
7) When finished, click OK and click Done
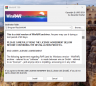

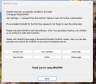
At the first launch, you can obtain a discount code if you choose to buy WinRAR

Main UI
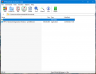
The main UI of WinRAR is very simple to use, because it has only the most features you need:
· Add files to an archive
· Extract files from an archive
· Test an archive
· View files in an archive
· Delete files from an archive
· Find files and archives
· Show information about files
· Repair an archive (in case you added a recovery record)
· A guided wizard
The main UI features a Windows-explorer based UI which lets you select files and folders for add them into an archive
The quick method to do some basic operations, is to use the Wizard, which lets you do these three things:
· Unpack an archive
· Create a new archive
· Add files to an existing archive
Let’s try to create a new archive with the wizard to see how to process is so easy to achieve:
1) Click the Wizard button from the main toolbar
2) Select “Create a new archive” and click on Next
3) Select files and folders and then click on OK
4) Click on “Browse” and select a path location and your desired name and click on Save and then Next (in my case is test.rar)
5) In the next page you can choose some additional options and even set a password to protect your archive
6) Let’s click on Finish
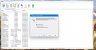
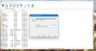
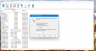
The Info function is very useful to see how much space you have saved with your archive and to see other useful details
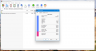
VirusScan uses the malware engines scans found on the local system; it is a useful function to protect against viruses and malwares. You can choose between Windows Defender, which is integrated into Windows, and a third-party tool.
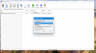
To protect an archive from potential corruption, click on the “Protect” button and then set a recovery record size to a size of your choice (remember that higher is the number and larger is the archive but the protection is also more). For sensible data it is advisable to set a large recovery size record. You can also lock an archive from modification (useful in case of a ransomware attack)
WinRAR has many options to let you configure it in the way you prefer, and you can even import/export settings, useful if you have multiple computers and want the same software configuration.
WinRAR has also an integrated Help containing many useful information and tips to help better understand how it works.

Wrapping things up, WinRAR is the best choice for who wants to create small and reliable archives, thanks to the many optimizations and features it has. And it is not a subscription-based software, so you need to upgrade only if you want or need it.
Useful resources
Official website: https://win-rar.com
Pricing: https://shop.win-rar.com/16/purl-shop-21...-startpage
WinRAR changelog: https://www.win-rar.com/whatsnew.html
WinRAR 7.00 64-bit version download (English): https://www.win-rar.com/fileadmin/winrar...64-700.exe
WinRAR 7.00 32-bit version download (English): https://www.win-rar.com/fileadmin/winrar...32-700.exe
EULA for WinRAR license: https://www.win-rar.com/winrarlicense.html
Download free WinRAR for Android 4.X and above (Free!): https://play.google.com/store/apps/detai...rarlab.rar
WinRAR is available in more than 40 languages around the world
Facebook: http://www.facebook.com/winrar
YouTube Channel: https://www.youtube.com/WinRAR-RARLAB


Win.rar GmbH is the official distributor on WinRAR and RARLabs products since 2002 and provides also the support for the products
|

|
|
| ChrisPC Free VPN Connection 4.24.0308 Released |
|
Posted by: mrtrout - 03-08-2024 , 10:45 PM - Forum: Freeware
- No Replies
|
 |
https://free-vpn-connection.chris-pc.com/index.html ChrisPCFree VPN Connection-Version History
Version 4.24.0308 (March 8,2024)
Added new servers from UK, France, Germany.
Improved support for Windows 11.
Fixed some minor bugs and errors. https://free-vpn-connection.chris-pc.com/index.html ChrisPC Free VPN Connection is a freeware software that helps you bypass region restricted websites, which means is absolutely free for non-commercial use. ChrisPC Free VPN Connection has many key features like:
Database with 90+ Free VPN servers from: USA, U.K., Germany, Canada, France, Germany, Russia, Singapore, Netherlands and Poland.
Bypass area restrictions of websites and have access to full content.
Get access to video websites such as: BBC iPlayer, ITV, Channel 4, Channel 5, UK TV Play, FOX, CNN, ABC, CBS, NBC, Crackle, Discovery, MTV, National Geographic, Showtime, AMC, USA, TNT, TBS, TCM, CW, Travel Channel, VH1, Syfy, TVNow, RTL, Prosieben, Sat 1, Sixx, Kabel1 and more.
Watch YouTube videos that are blocked in your country.
Access your Twitter account without problems or get in touch with your Facebook friends.
Watch all your favorite TV programmes from outside the USA, U.K., Germany, Canada, France, Germany, Russia, Singapore, Netherlands and Poland.
Support for all browsers.
Launch software on Windows boot.
Minimize ChrisPC Free VPN Connection to systray.
WhataretheSystemRequirements?
Hardware:
1500 MHz processor or higher, such as an Intel Dual-Core Processors
Memory : more than 1 GB RAM
HDD Space : 15 MB
Software:
Windows XP, Microsoft Vista, Windows 7, Windows 8, Windows 10 or Windows 11.
Edge, Internet Explorer 7 or higher, Firefox 3 or higher, Google Chrome, Safari.
Last Update: March 8, 2024 Download: https://www.chris-pc.com/downloadN.php?i...ection.exe ChrisPC Free VPN Connection Setup Application Reputation Trusted (Digital Signature) Digital Signature; ChrisPC Software SRL Sign Date: 2024-03-08 10:17 AM https://opentip.kaspersky.com/https%3A%2...tab=lookup Report
Report for web address
https://free-vpn-connection.chris-pc.com/index.html
Good
Overview
IPv4 count ≈ 12
Files count —
Created
9 Dec, 2003
17:00
Expires
9 Dec, 2024
17:00
Domain free-vpn-connection.chris-pc.com
Registration organization —
Registrar name Name.com, Inc. Kaspersky Threat Intelligence Portal ChrisPC Free VPN Connection 4.24.0308 is 100% Clean, which means it does not contain any form of malware, including but not limited to: spyware, viruses, trojans and backdoors. is 100% Scanned Malware Free & Clean & Safe With Kaspersky Standard 2024 https://www.kaspersky.com/standard Our triple-layer protection system works 24/7 to secure your devices and data. It blocks common and complex threats like viruses, malware, ransomware, spy apps, and all the latest hacking techniques.
Antivirus
Real-time Antivirus protects you from common threats like worms and trojans, as well as from more sophisticated threats like botnets and rogues.
Anti-Malware
Advanced anti-malware blocks threats like keyloggers, adware, spear phishing, rootkits, and man-in-the-middle attacks.
Anti-Hacking
Anti-ransomware and network security controls stop hackers from infiltrating your home network and stealing your data.
|

|
|
| KASPERSKY GLOBAL TRANSPARENCY INITIATIVE |
|
Posted by: mrtrout - 03-08-2024 , 02:39 PM - Forum: Security News
- No Replies
|
 |
https://www.kaspersky.com/transparency-center KASPERSKY GLOBAL TRANSPARENCY INITIATIVE
Today, transparency is a vital element in the digital world we all rely on. Kaspersky Global Transparency Initiative includes a number of actionable and concrete measures to engage with the wider cybersecurity community and stakeholders in validating and verifying the trustworthiness of its products, internal processes and business operations. DATA, INDEPENDENT REVIEWS AND MORE...
Within the framework of our Global Transparency Initiative we have relocated our cyberthreat-related data storage and processing for a number of regions to Switzerland. We have also opened our first Transparency Center in the country.
User Data
Threat-related data received from users of Kaspersky products in Europe, North and Latin America, the Middle East, and also several countries in Asia-Pacific is processed and stored on Swiss servers.
Transparency Center
A facility for trusted partners and government stakeholders to review the company's code, software updates and threat detection rules. The company opened Transparency Centers in Kigali (Rwanda), Kuala Lumpur (Malaysia), Madrid (Spain), Riyadh (Saudi Arabia), Rome (Italy), São Paulo (Brazil), Singapore, Tokyo (Japan), Utrecht (the Netherlands), Woburn (the United States), and Zurich (Switzerland).
Independent review
Third-party assessment of internal processes to verify the integrity of Kaspersky solutions and processes:
• SOC 2 audit, conducted by an independent accounting firm;
• ISO 27001 certification for data security systems. TRANSPARENCY CENTERS
Transparency Centers serve as facilities for trusted partners to access reviews of the company’s code, software updates and threat detection rules, along with other activities. Through them, we provide governments and partners with information on our products and their security, including essential and important technical documentation, for external evaluation in a secure environment. They also serve as a briefing center where trusted stakeholders can learn more about the company’s portfolio, engineering and data processing practices.
Kaspersky Transparency Centers are operating in Kigali, Kuala Lumpur, Madrid, Riyadh, Rome, São Paulo, Singapore, Tokyo, Utrecht, Woburn, and Zurich.
At Kaspersky’s Transparency Centers, the company provides the opportunity to compile its software from the source code and compare it with the publicly available one.
No other cybersecurity provider has done anything as far reaching as this. In opening its Transparency Centers, Kaspersky makes a significant step towards becoming completely transparent about its protection technologies, infrastructure and data processing practices.
The Transparency Centers’ services are also available for remote access. To request access to the Transparency Center, please contact TransparencyCenter@kaspersky.com or visit the website . INDEPENDENT AUDIT
Kaspersky continuously undertakes third-party assessments to verify the integrity of its solutions and processes. The company has successfully completed the Service Organization Control for Service Organizations (SOC 2) Type 2 audit, conducted by an independent accounting firm.
The final report confirms that the development and release of Kaspersky’s threat detection rules databases (AV databases) are protected from unauthorized changes by strong security controls. To learn more and to request the Kaspersky SOC 2 Type 2 Report, please visit the website.
Kaspersky has also attained ISO27001 certification for its data services.
THE NEXT LEVEL OF DATA PROTECTION!
While Kaspersky’s current data protection practices are implemented in accordance with the highest industry standards and provide an extremely high level of security for any information processed by the company’s products and services, the company continuously improves its procedures for the protection of its customers’ data.
Malicious and suspicious files voluntarily shared by users of Kaspersky products in Europe, North and Latin America, the Middle East, and also several countries in Asia-Pacific are processed and stored in two data centers in Zurich. These provide world-class facilities in compliance with industry standards to ensure the highest levels of security.
In addition, it has been certified that Kaspersky applies a management system in line with the ISO/IEC 27001:2013 standard in the delivery of malicious and suspicious files using Kaspersky Security Network (KSN) infrastructure, as well as safe storage and access to these files in the company’s Distributed File System (KLDFS). In 2022, Kaspersky’s data services were re-certified with extended scope, with data services for both cyberthreat-related data and statistics now being covered by the certification. This include the company’s data centers in Zurich, Switzerland; Frankfurt, Germany; Toronto, Canada; and Moscow, Russia.
https://www.kaspersky.com/transparency-center KASPERSKY GLOBAL TRANSPARENCY INITIATIVE
Today, transparency is a vital element in the digital world we all rely on. Kaspersky Global Transparency Initiative includes a number of actionable and concrete measures to engage with the wider cybersecurity community and stakeholders in validating and verifying the trustworthiness of its products, internal processes and business operations. DATA, INDEPENDENT REVIEWS AND MORE...
Within the framework of our Global Transparency Initiative we have relocated our cyberthreat-related data storage and processing for a number of regions to Switzerland. We have also opened our first Transparency Center in the country.
User Data
Threat-related data received from users of Kaspersky products in Europe, North and Latin America, the Middle East, and also several countries in Asia-Pacific is processed and stored on Swiss servers.
Transparency Center
A facility for trusted partners and government stakeholders to review the company's code, software updates and threat detection rules. The company opened Transparency Centers in Kigali (Rwanda), Kuala Lumpur (Malaysia), Madrid (Spain), Riyadh (Saudi Arabia), Rome (Italy), São Paulo (Brazil), Singapore, Tokyo (Japan), Utrecht (the Netherlands), Woburn (the United States), and Zurich (Switzerland).
Independent review
Third-party assessment of internal processes to verify the integrity of Kaspersky solutions and processes:
• SOC 2 audit, conducted by an independent accounting firm;
• ISO 27001 certification for data security systems. TRANSPARENCY CENTERS
Transparency Centers serve as facilities for trusted partners to access reviews of the company’s code, software updates and threat detection rules, along with other activities. Through them, we provide governments and partners with information on our products and their security, including essential and important technical documentation, for external evaluation in a secure environment. They also serve as a briefing center where trusted stakeholders can learn more about the company’s portfolio, engineering and data processing practices.
Kaspersky Transparency Centers are operating in Kigali, Kuala Lumpur, Madrid, Riyadh, Rome, São Paulo, Singapore, Tokyo, Utrecht, Woburn, and Zurich.
At Kaspersky’s Transparency Centers, the company provides the opportunity to compile its software from the source code and compare it with the publicly available one.
No other cybersecurity provider has done anything as far reaching as this. In opening its Transparency Centers, Kaspersky makes a significant step towards becoming completely transparent about its protection technologies, infrastructure and data processing practices.
The Transparency Centers’ services are also available for remote access. To request access to the Transparency Center, please contact TransparencyCenter@kaspersky.com or visit the website . INDEPENDENT AUDIT
Kaspersky continuously undertakes third-party assessments to verify the integrity of its solutions and processes. The company has successfully completed the Service Organization Control for Service Organizations (SOC 2) Type 2 audit, conducted by an independent accounting firm.
The final report confirms that the development and release of Kaspersky’s threat detection rules databases (AV databases) are protected from unauthorized changes by strong security controls. To learn more and to request the Kaspersky SOC 2 Type 2 Report, please visit the website.
Kaspersky has also attained ISO27001 certification for its data services.
THE NEXT LEVEL OF DATA PROTECTION!
While Kaspersky’s current data protection practices are implemented in accordance with the highest industry standards and provide an extremely high level of security for any information processed by the company’s products and services, the company continuously improves its procedures for the protection of its customers’ data.
Malicious and suspicious files voluntarily shared by users of Kaspersky products in Europe, North and Latin America, the Middle East, and also several countries in Asia-Pacific are processed and stored in two data centers in Zurich. These provide world-class facilities in compliance with industry standards to ensure the highest levels of security.
In addition, it has been certified that Kaspersky applies a management system in line with the ISO/IEC 27001:2013 standard in the delivery of malicious and suspicious files using Kaspersky Security Network (KSN) infrastructure, as well as safe storage and access to these files in the company’s Distributed File System (KLDFS). In 2022, Kaspersky’s data services were re-certified with extended scope, with data services for both cyberthreat-related data and statistics now being covered by the certification. This include the company’s data centers in Zurich, Switzerland; Frankfurt, Germany; Toronto, Canada; and Moscow, Russia. https://opentip.kaspersky.com/https%3A%2...tab=lookup Report
Report for web address
https://www.kaspersky.com/transparency-center
Good
Overview
IPv4 count ≈ 1,000
Files count —
Created
8 Oct, 1997
17:00
Expires
6 Oct, 2024
18:00
Domain kaspersky.com
Registration organization Joint Stock Company Kaspersky Lab
Registrar name Regional Network Information Center, JSC dba RU-CENTER
|

|
|
| How to Use WD Easystore on Mac? [Format & Time Machine] |
|
Posted by: ppp2da - 03-08-2024 , 04:20 AM - Forum: Guides, Tips & Tricks
- Replies (1)
|
 |
Quote:
Summary: This article explains how to use Easystore on Mac, including how to format a WD Easystore for Mac or both Mac and PC, back up your Mac to Easystore, and fix WD Easystore not working on Mac.
WD Easystore drives are generally considered a popular choice for external storage needs. But if you're new to them, you may want to learn how to set up a WD Easystore external hard drive on your Mac. Or, if you have been using one for a while but it suddenly stopped working, you'll want to find the solutions.
This guide will elaborate on issues you may encounter when working with an Easystore drive on your Mac and help you use it efficiently.
Guide on how to use WD Easystore on Mac:
1. How to use WD Easystore on Mac?
2. How to read/write to WD Easystore on Mac without formatting?
3. How to format WD Easystore for Mac?
4. How to format Easystore for Mac and PC?
5. How to use Time Machine on Mac with Easystore?
6. How to fix WD Easystore not showing up/not working on Mac?
7. FAQs about how to use WD Easystore on Mac
Continue reading here:
How to Use WD Easystore on Mac
H
|

|
|
| AI and Machine Learning in Cybersecurity How They Will Shape the Future |
|
Posted by: mrtrout - 03-06-2024 , 07:18 PM - Forum: Security News
- No Replies
|
 |
https://www.kaspersky.com/resource-cente...ersecurity AI and Machine Learning in Cybersecurity — How They Will Shape the Future AI, Machine learning, and Deep learning definition within cybersecurity
AI cybersecurity, with the support of machine learning, is set to be a powerful tool in the looming future. As with other industries, human interaction has long been essential and irreplaceable in security. While cybersecurity currently relies heavily on human input, we are gradually seeing technology become better at specific tasks than we are.
Every technology improvement brings us slightly closer to supplementing human roles more effectively. Among these developments, a few areas of research are at the core of it all:
Artificial intelligence (AI) is designed to give computers the full responsive ability of the human mind. This is the umbrella discipline under which many others fall, including machine learning and deep learning.
Machine learning (ML) uses existing behavior patterns, forming decision-making based on past data and conclusions. Human intervention is still needed for some changes. Machine learning is likely the most relevant AI cybersecurity discipline to date.
Deep learning (DL) works similarly to machine learning by making decisions from past patterns but makes adjustments on its own. Deep learning in cybersecurity currently falls within the scope of machine learning, so we’ll focus mostly on ML here.
What AI and machine learning can do for cybersecurity
AI and cybersecurity have been touted as revolutionary and much closer than we might think. However, this is only a partial truth that must be approached with reserved expectations. The reality is that we may be faced with relatively gradual improvements for the future to come. In perspective, what may seem gradual when compared to a fully autonomous future is actually still leaps beyond what we’ve been capable of in the past.
As we explore the possible implications with security in machine learning and AI, it’s important to frame the current pain points in cybersecurity. There are many processes and aspects we’ve long accepted as normal that can be treated under the umbrella of AI technologies.
Human error in configuration
Human error is a significant part of cybersecurity weaknesses. For example, the proper system configuration can be incredibly difficult to manage, even with large IT teams engaging in setup. In the course of constant innovation, computer security has become more layered than ever. Responsive tools could help teams find and mitigate issues that appear as network systems are replaced, modified, and updated.
Consider how newer internet infrastructure like cloud computing may be stacked atop older local frameworks. In enterprise systems, an IT team will need to ensure compatibility to secure these systems. Manual processes for assessing configuration security cause teams to feel fatigued as they balance endless updates with normal daily support tasks. With smart, adaptive automation, teams could receive timely advice on newly discovered issues. They could get advice on options for proceeding, or even have systems in place to automatically adjust settings as needed.
Human efficiency with repeated activities
Human efficiency is another pain point within the cybersecurity industry. No manual process is perfectly repeatable every time, especially in a dynamic environment such as ours. The individual setup of an organization’s many endpoint machines is among the most time-consuming tasks. Even after initial setup, IT teams find themselves revisiting the same machines later on for correcting misconfigurations or outdated setups that cannot be patched in remote updates.
Furthermore, when employees are tasked with responses to threats, the scope of said threat can rapidly shift. Where human focus may be slowed by unexpected challenges, a system based on AI and machine learning can move with minimal delay.
Threat alert fatigue
Threat alert fatigue gives organizations another weakness if not handled with care. Attack surfaces are increasing as the aforementioned layers of security become more elaborate and sprawling. Many security systems are tuned to react to many known issues with a barrage of purely reflexive alerts. As a result, these individual prompts leave human teams to parse out potential decisions and take action.
A high influx of alerts makes this level of decision-making an especially taxing process. Ultimately, decision fatigue becomes a daily experience for cybersecurity personnel. Proactive action for these identified threats and vulnerabilities is ideal, but many teams lack the time and staffing to cover all their bases.
Sometimes teams have to decide to confront the largest concerns first and let the secondary objectives fall to the wayside. Using AI within cybersecurity efforts can allow IT teams to manage more of these threats in an effective, practical fashion. Confronting each of these threats can be made much easier if batched by automated labeling. Beyond this, some concerns may actually be able to be treated by the machine learning algorithm itself.
Threat response time
Threat response time is absolutely among the most pivotal metrics for a cybersecurity teams’ efficacy. From exploitation to deployment, malicious attacks have been known to move very quickly. Threat actors of the past used to have to sift through network permissions and disarm security laterally for sometimes weeks on end before launching their attack.
Unfortunately, experts in the cyber defense space are not the only ones benefiting from technology innovations. Automation has since become more commonplace in cyber attacks. Threats like the recent LockBit ransomware attacks have accelerated attack times considerably. Currently, some attacks can even move as quick as half-an-hour.
The human response can lag behind the initial attack, even with known attack types. For this reason, many teams have more often engaged in reactions to successful attacks rather than preventions of attempted attacks. On the other end of the spectrum, undiscovered attacks are a danger all their own.
ML-assisted security can pull data from an attack to be immediately grouped and prepared for analysis. It can provide cybersecurity teams with simplified reports to make processing and decision-making a cleaner job. Going beyond just reporting, this type of security can also offer recommended action for limiting further damage and preventing future attacks.
New threat identification and prediction
New threat identification and prediction serve as another factor that impacts response timeframes for cyber attacks. As noted previously, lag time already occurs with existing threats. Unknown attack types, behaviors, and tools can further deceive a team into slow reactions. Worse, quieter threats like data theft can sometimes go completely undiscovered. An April 2020 survey by Fugue gathered that roughly 84% of IT teams were concerned over their cloud-based systems being hacked without their awareness.
Constant attack evolution leading to zero-day exploits is always an underlying concern within network defense efforts. But for some good news, cyber attacks are not commonly built from scratch. Being that they are often constructed atop behaviors, frameworks, and source codes of past attacks, machine learning has a pre-existing path to work from.
Programming based in ML can help highlight commonalities between the new threat and previously identified ones to help spot an attack. This is something that humans cannot effectively do within a timely fashion and further highlights that adaptive security models are necessary. From this viewpoint, machine learning can potentially make it easier for teams to also predict new threats and reduce lag time due to increased threat awareness.
Staffing capacity
Staffing capacity falls under the scope of ongoing issues plaguing many IT and cybersecurity teams globally. Depending on the needs of an organization, the number of qualified professionals can be limited.
However, the more common situation is that hiring human help can also cost organizations a healthy amount of their budget. Supporting human staff requires not only compensating for daily labor but providing assistance in their ongoing need for education and certification. Staying current as a cybersecurity professional is demanding, especially in regard to the perpetual innovation that we’ve continued to mention throughout the discussion thus far.
AI-based security tools can take the lead with a less dense team to staff and support it. While this staff will need to keep up with the cutting-edge areas of AI and machine learning, cost and time savings will come alongside the smaller staffing requirements.
Adaptability
Adaptability is not as obvious of a concern as other point mentioned but can shift the abilities of an organization’s security dramatically. Human teams may be lacking in their capacity to customize their skill set to your specialized requirements.
If the staff is not trained in specific methods, tools, and systems, you may find that your team’s effectiveness is stunted as a result. Even seemingly simple needs like adopting new security policies can move slowly with human-based teams. This is just the nature of being human, as we cannot learn new ways of doing things instantly and must have time to do so. With the right datasets, aptly trained algorithms can be morphed to be a bespoke solution specifically for you.
machine learning in cybersecurity
How AI is used in cybersecurity
Artificial intelligence in cybersecurity is considered to be a superset of disciplines like machine learning and deep learning cyber security, but it does have its own role to play.
AI at its core is concentrated on “success” with “accuracy” carrying less weight. Natural responses in elaborate problem-solving are the ultimate goal. In a true execution of AI, actual independent decisions are being made. Its programming is designed for finding the ideal solution in a situation, rather than just the hard-logical conclusion of the dataset.
To further explain, it’s best to understand how modern AI and its underlying disciplines work currently. Autonomous systems are not within the scope of widely mobilized systems, especially in the field of cybersecurity. These self-directed systems are what many people commonly associate with AI. However, AI systems that either assist or augment our protective services are practical and available.
The ideal role of AI in cybersecurity is the interpretation of the patterns established by machine learning algorithms. Of course, it's not yet possible for modern-day AI to interpret results with the abilities of a human yet. Work is being done to help develop this field in pursuit of humanlike frameworks, but true AI is a distant goal that requires machines to take abstract concepts across situations to reframe them. In other words, this level of creativity and critical thought is not as close as the AI rumors would like you to believe.
How machine learning is used in cybersecurity
Machine learning security solutions are different from what people envision to be of the artificial intelligence family. That said, they are easily the strongest cybersecurity AI tools we have to-date. In the scope of this technology, data patterns are used to reveal the likelihood that an event will occur — or not.
ML is somewhat opposite to that of true AI in some respects. Machine learning is particularly “accuracy” driven, but not as focused on “success.” What this means is that ML proceeds intending to learn from a task-focused dataset. It concludes by finding the most optimal performance of the given task. It will pursue the only possible solution based on the given data, even if it’s not the ideal one. With ML, there is no true interpretation of the data, which means this responsibility still falls on human task forces.
Machine learning excels at tedious tasks like data pattern identification and adaptation. Humans are not well suited to these types of tasks due to task fatigue and a generally low tolerance for monotony. So, while the interpretation of data analysis is still in human hands, machine learning can assist in framing the data in a readable, dissection-ready presentation. Machine learning cybersecurity comes in a few different forms, each with its own unique benefits:
Data classifying
Data classifying works by using preset rules to assign categories to data points. Labeling these points is an important part of building a profile on attacks, vulnerabilities, and other aspects of proactive security. This is fundamental to the intersection of machine learning and cyber security.
Data clustering
Data clustering takes the outliers of classifying preset rules, placing them into “clustered” collections of data with shared traits or odd features. For example, this can be used when analyzing attack data that a system is not already trained for. These clusters can help determine how an attack happened, as well as, what was exploited and exposed.
Recommended courses of action
Recommended courses of action elevate the proactive measures of an ML security system. These are advisories based around behavior patterns and former decisions, providing naturally suggested courses of action. It is important to restate here that this is not intelligent decision making via true autonomous AI. Rather, it’s an adaptive conclusion framework that can reach through preexisting data points to conclude logical relationships. Responses to threats and mitigating risks can be assisted immensely by this type of tool.
Possibility synthesis
Possibility synthesis allows for the synthesizing of brand-new possibilities based on lessons from previous data and new unfamiliar datasets. This is a bit different from recommendations, as it is concentrating more on the chances that an action or the state of a system falls in line with similar past situations. For example, this synthesis can be used for a preemptive probing of weak points in an organization’s systems.
Predictive forecasting
Predictive forecasting is the most forward-thinking of the ML component processes. This benefit is achieved by predicting potential outcomes by evaluating existing datasets. This can be used primarily for building threat models, outlining fraud prevention, data breach protection, and is a staple of many predictive endpoint solutions.
Examples of machine learning in cybersecurity
To explain further, here are a few examples that underline the value of machine learning as it pertains to cybersecurity:
Data privacy classification and compliance
Protecting your organization from violations of privacy laws has likely risen to be a top priority over the past few years. With the General Data Protection Regulation (GDPR) leading the way, other legal measures have appeared such as the California Consumer Protection Act (CCPA).
Managing the collected data of your customers and users must be done under these acts, which usually means this data must be accessible for deletion upon request. The consequences of not following these legislations include hefty fines, as well as, damage to your organization’s reputation.
Data classifying can help you separate identifying user data from that which is anonymized or identify-free. This saves you from manual labor in attempts to parse out vast collections of old and new data, especially in large or older organizations.
User behavior security profiles
By forming custom profiles on network staff based around user behaviors, security could be tailor-made to fit your organization. This model can then establish what an unauthorized user might look like based on the outliers of user behavior. Subtle traits like keyboard strokes can form a predictive threat model. With the outline of possible outcomes of potential unauthorized user behaviors, ML security can suggest recommended recourse to reduce exposed attack surfaces.
System performance security profiles
Similar to the user behavior profile concept, a custom diagnostic profile of your entire computer’s performance can be compiled when healthy. Monitoring the processor and memory use alongside traits like high internet data use can be indicative of malicious activity. That said, some users may regularly use high volumes of data through video conferencing or frequent large media file downloads. By learning what a system’s baseline performance generally looks like, it can establish what it should not look like, similar to the user behavior rules we mentioned in an earlier ML example.
Behavior-based bot blocking
Bot activity can be an inbound bandwidth drain for websites. This is especially true for those that depend on internet-based business traffic, such as those with dedicated e-commerce storefronts and no brick-and-mortar locations. Authentic users may have a sluggish experience that causes a loss of traffic and business opportunity.
By classifying this activity, ML security tools can block the bots’ web, regardless of tools used like virtual private networks that can anonymize them. Behavioral data points on the malicious parties can help a machine learning security tool form predictive models around this behavior and preemptively block new web addresses for displaying this same activity.
The Future of Cybersecurity
Despite all the glowing dialogue around the future of this form of security, there are still limitations to be noted.
ML needs datasets but may conflict withdata privacylaws. Training software systems requires plenty of data points to build accurate models, which doesn’t meld well with “the right to be forgotten.” The human identifiers of some data may cause violations, so potential solutions will need to be considered. Possible fixes include getting systems to either make original data virtually impossible to access once software has been trained. Anonymizing data points is also in consideration, but this will need to be examined further to avoid skewing the program logic.
The industry needs more AI and ML cybersecurity experts capable of working with programming in this scope. Machine learning network security would benefit greatly from staff that can maintain and adjust it as needed. However, the global pool of qualified, trained individuals is smaller than the immense global demand for staff that can provide these solutions.
Human teams will still be essential. Finally, critical thinking and creativity are going to be vital to decision-making. As mentioned much earlier, ML is not prepared or capable of doing either, and neither is AI. To continue this thread, you’ll have to use these solutions to augment your existing teams.
3 Tips for embracing the future of cybersecurity
On the road to artificial intelligence security, there are a few steps you can take to get yourself closer to the future:
Invest in staying future-focused with your technology. The costs of being exploited due to outdated technology or using redundant manual labor will be far greater as threats become more elaborate. Staying ahead of the curve can help mitigate some risk. By using forward-thinking solutions such as Kaspersky Integrated Endpoint Security, you’ll be more prepared to adapt.
Supplement your teams with AI and ML, do not replace them. Vulnerabilities will still exist, as no system on the market today is foolproof. Since even these adaptive systems can be deceived by clever attack methods, be sure your IT team learns to work with and support this infrastructure.
Routinely update your data policies to comply with evolving legislation. Data privacy has become a focal point for governing bodies across the globe. As such, it will remain among the top points of concern for most enterprises and organizations for the foreseeable future. Be sure that you are keeping per the most recent policies.
|

|
|
| WinRAR 7.0X review needed |
|
Posted by: tarekma7 - 03-05-2024 , 07:22 PM - Forum: Reviewer Needed
- Replies (1)
|
 |
Hi All
I need any member who is interested to prepare a review for WinRAR v7.0X
The reviewer will get a lifetime Perpetual license with minor updates v7.0x (No Major upgrades)
Reply here or PM me if you are interested
|

|
|
| Emotional Recorder from fracturesounds for Kontakt [for free] |
|
Posted by: ahmed - 03-04-2024 , 12:57 PM - Forum: External Giveaways/Freebies
- No Replies
|
 |
![[Image: 6RRWAZl.jpg]](https://i.imgur.com/6RRWAZl.jpg)
Uplift your compositions with this breathtaking descant recorder. Deep sampled in glorious detail, with stunning true-legato.
After over 5 years of development, we are proud to present Emotional Recorder. Performed by renowned recorder virtuoso Will Bedford, this prestinely sampled instrument captures the true essence of the descant recorder, with heartfelt emotion injected into each note. Magnificently sampled into a passionate and receptive instrument, Emotional Recorder transforms any piece through its ability to encapsulate raw, unencumbered feeling.
The library features a groundbreaking true legato engine, with a unique ‘emotion’ control for embellishing the performance with ornaments and natural artifacts which bring the performance to life.
This is underpinned by the inbuilt breath controls, which offer the ability to add natural breaths between phrases, enhancing the realism of the performance.
The humble descant recorder has been long underrepresented in the sampling world, and we hope this library will find a home in your toolkit and enrich your music for years to come.
(Available at a generous intro price until April 1st.)
Visit:
https://fracturesounds.com/product/emotional-recorder/
|

|
|
| Hybrid 2024.03.03.1 |
|
Posted by: Mohammad.Poorya - 03-04-2024 , 12:53 PM - Forum: Freeware
- No Replies
|
 |
Changes in Hybrid 2024.03.03.1:
*fixed* - Avisynth: (32bit) SplineResize100/144 calls
- Vapoursynth: custom section hinting accidentally required ‘# # …’ instead of ‘# …’
- Vapoursynth: allow lowering frame rate with rife
- Vapoursynth: detect ‘2020 non .. ‘ as ‘2020cl’
- Vapoursynth: crop in compare view
- NoXSynth: fix subtitle embedding by changing local.conf handling
- ui: subtitle controls enabled, even when no subititles are available
*added*- Subtitle: Support embedding subtitle when QSVEncC/NVEncC with ‘only use encoder’ is used.
- Torch: added DeOldify through vs-deoldify
*changed*- Muxing/Extraction: Force FFmpeg for dts/dts-hd audio when dealing with mp4 containers.
- Subtitle: Subtitle language passthrough handling.
- Input: Support Gray8 input images.
Size: 1.28 GB
DOWNLOAD Hybrid for Windows
DOWNLOAD Hybrid Linux64bit
DOWNLOAD Hybrid Linux64bit (with base tools and most dependencies)
|

|
|
| Vovsoft JSON to CSV Converter v 1.1 [for PC] |
|
Posted by: ahmed - 03-04-2024 , 12:37 PM - Forum: External Giveaways/Freebies
- No Replies
|
 |
![[Image: json-to-csv-converter.png?v=1.1]](https://vovsoft.com/screenshots/json-to-csv-converter.png?v=1.1)
Vovsoft JSON to CSV Converter is a user-friendly desktop application designed to streamline the process of converting JSON (JavaScript Object Notation) files into CSV (Comma-Separated Values) format. This software is an essential tool for data analysts, developers, and anyone who needs to manipulate and analyze data stored in JSON format, enabling them to convert it into a more universally accepted and spreadsheet-friendly CSV format.
Key Features: - Vovsoft JSON to CSV Converter is a user-friendly desktop application designed to efficiently convert JSON files to CSV.
- You are allowed to select delimiter characters to ensure compatibility with various CSV parsing requirements and decide to include or exclude column headers in the CSV output.
- By supporting ANSI and UTF-8 encodings, this program ensures that the CSV output will keep the correct characters and formatting for different languages and regions.
- The nested JSON structures, arrays, and complex data types can be handled and then transformed into a flat CSV structure with the help of this converter tool.
- In just a few simple clicks, you can efficiently convert multiple JSON files to CSV format at once.
- It works well with spreadsheet platforms like Microsoft Excel and Google Sheets to optimize performance, providing fast conversion speeds even for large JSON files.
System Requirements:
Supports Windows 11, Windows 10, Windows 8/8.1, Windows 7, Windows Vista, Windows XP (64-bit)
Homepage:
https://vovsoft.com/software/json-to-csv-converter/
License:
Lifetime license,No free updates!
GP:
https://vovsoft.com/giveaway/free-json-t...rter-2024/
License:
► Campaign Start: March 3, 2024
► Campaign End: March 10, 2024
|

|
|
| 5 Cloud-Based Antivirus Software That Actually Stop 2024's Cyberthugs |
|
Posted by: mrtrout - 03-04-2024 , 11:43 AM - Forum: Video Reviews
- Replies (1)
|
 |
https://www.youtube.com/watch?v=hYbbxyaZEYI Malware Mayhem? 5 Cloud-Based Antivirus Software That Actually Stop 2024's Cyberthugs
TheDroidGuy
165K subscribers
31 views Jan 5, 2024 #CyberSecurity #DigitalSafety
As the digital landscape evolves, so does our need for advanced cybersecurity. Say goodbye to resource-heavy desktop antivirus – enter cloud-based solutions! ?️ This video breaks down the top contenders in 2024, helping you choose the perfect shield for your digital life.
?️ Cloud-Based Antivirus: A Modern Approach to Security:
Explore how traditional antivirus compares to the modern cloud-based approach.
Learn the benefits, including lightweight scans, real-time threat detection, centralized management, and automatic updates.
? Top Cloud-Based Antivirus Contenders:
TotalAV: Championing overall value with impressive malware detection and bonus features.
Surfshark AV: A newcomer bundling antivirus with a high-speed VPN for privacy-conscious users.
NordVPN TP: Robust security with a user-friendly interface and excellent customer support.
McAfee: A trusted name offering lightweight and effective cloud-based security, plus identity theft protection.
Avira: Free yet powerful, Avira Free Antivirus provides surprisingly good cloud-based protection.
? Choosing the Right Cloud-Based Antivirus:
Consider your priorities: raw protection, bonus features, or affordability?
Ensure compatibility across all your devices.
Opt for a user-friendly interface for a smooth experience.
? Important Reminder:
While cloud-based antivirus is powerful, it's not a magic bullet. Practice safe browsing habits, stay cautious of suspicious links, and always keep your software updated for a robust defense against cyber threats. Your digital safety matters! ?? #CyberSecurity #CloudAntivirus #DigitalSafety McAfee WebAdvisor Website status:
Safe
www.youtube.com/watch
We combed through this website and everything looks good to us. You're safe!
info-
Media Sharing
info-
Streaming Media
|

|
|
| ACDSee Free 2.2.0.604 Freeware New Released |
|
Posted by: mrtrout - 03-03-2024 , 05:46 PM - Forum: Freeware
- No Replies
|
 |
https://www.acdsee.com/en/products/acdsee-free/
A BETTER WAY TO BROWSE
ACDSee Free is a fast and powerful file browser, ideal for viewing RAW images, as well as searching and sorting your media libraries. https://www.acdsee.com/en/products/acdse...thank-you/ Download Free: https://dl.acdsystems.com/acdsee-free/en...e-free.exe What can ACDSee Free do for you?
View RAW Camera File Formats
RAW image files can be thought of as digital negatives, and with ACDSee Free, RAW files can be viewed just the same as other image files, like JPEG or PNG.
Quickly Load Thousands of Photos
No tedious importing! ACDSee Free connects directly to your computer drives, so you can search, sort, and view your photos instantly.
Easily Create Slideshows
Select the files you want to see, then sit back and watch the journey unfold.
Batch Rotate and Flip
Experience the time-saving power of batch processing by rotating and flipping multiple photos at the same time.
Click & Share with SendPix™
Built by ACDSee, SendPix™ is a free media sharing app seamlessly incorporated into ACDSee Free. Select and send to share memories with family and friends.
View a Plethora of File Types
Your media collection covers many file types from various devices. In addition to photos, you can also view videos, Microsoft Office™ documents, PDFs, and play audio files.
What else does ACDSee Free do?
Convenient Printing
Easily print your memories right from ACDSee Free as single images. You can also generate a contact/proof sheet for an overview of many images.
Speedy Viewing
Use Quick View to rapidly scroll through thousands of images.
Helpful Searching
With Quick Search you can tailor your search results based on file names and folder contents. You can also use the Sort menu to further refine image searches by Image Type, File Size, Date Taken, and Date Modified.
Personalization
Want to be inspired by a favorite photo? Use ACDSee Free to set your device’s wallpaper.
Gain Perspective
Use the intuitive Zoom In/Out tools to inspect image details. McAfee WebAdvisor Website status:
Safe
www.acdsee.com/en/products/acdsee-free/
We combed through this website and everything looks good to us. You're safe! ACDSee Free 2.2.0.604 Freeware is 100% Clean, which means it does not contain any form of malware, including but not limited to: spyware, viruses, trojans and backdoors. Was 100% Scanned Malware Free & Clean & Safe With McAfee Total Protection 2024 McAfee Total Protection provides our award-winning antivirus to defend against viruses, online threats, and ransomware with both cloud-based online and offline protection. Confidently bank, shop, or simply just browse online with AI-powered device protection that keeps your personal information safe from new and evolving threats. Digital Signature: ACD Systems International Inc. https://www.acdsee.com/en/about/ About ACDSee
Where it All Started
From developing one of the world’s first digital asset managers to engineering the world’s first digital asset manager and RAW editor with layers, to more recent innovations such as advanced Artificial Intelligence tools, ACDSee has been on the cutting edge of creative software since 1994.
Branching out from image viewing, digital asset management, format conversion, relational databases, and cataloging, to image editing, plug-ins, support for RAW images, online functionality, image manipulation, video recording and editing, layered editing, mobile apps, and much more, ACDSee has evolved each and every year since its inception. Recently, ACDSee has taken a deep dive into enhancing existing features with AI to make tedious tasks a thing of the past.
After three decades of software innovation, the ACDSee brand now serves individuals and businesses in every corner of the globe. McAfee WebAdvisor Website status:
Safe
www.acdsee.com/en/about/
We combed through this website and everything looks good to us. You're safe!
|

|
|
| BurnAware Free 17.5 New Released |
|
Posted by: mrtrout - 03-01-2024 , 01:22 AM - Forum: Freeware
- No Replies
|
 |
https://www.burnaware.com/whats-new.html What's new?
BurnAware v17.5
Released February 29, 2024
New features
• Copy to ISO tool replaced with Backup Disc tool.
Enhancements
• Updated user interface and translations.
• Improved audio encoding and tag reading.
• Improved data reading in Data Recovery tool.
Bug fixes
• Resolved problem with session reading from Multisession disc.
• Resolved issue with possible memory leak in Data Recovery tool. https://www.burnaware.com/download.html Download https://www.burnaware.com/downloads/burn...e_17.5.exe
BurnAware Free 17.5
Free version (23.9 MB)
✓ 32-bit only
✓ Disc burning tools
✓ ISO making and burning
✓ For personal use only
Web Protection by Bitdefender
This page is safe
We did not find any suspicious elements on this page. https://www.burnaware.com/download.html
Norton Rating:
Safe
This website is considered safe. BurnAware Free 17.5 (Bitdefender`s unbeatable multi-layered protection keeps your devices safe from all new and existing e-threats.) ( Bitdefender Total Security works against all e-threats, from viruses, worms and Trojans, to ransomware, zero-day exploits, rootkits and spyware. ) (The new cyber threat intelligence technologies included can analyze and identify suspicious network-level activities, and block sophisticated exploits, malware- and botnet-related URLs, and brute force attacks.) ( Cryptomining Protection NEW: Don’t be the victim of bad guys who make money with your hardware and without your consent, while inflating your electricity bills. Protect yourself against “leech” software that run on your system without your knowledge.) BurnAware v17.5 Free is 100% CLEAN, which means it does not contain any form of malware, including adware, spyware, viruses, trojans and backdoors. & Was 100% Scanned Malware Free & Clean With Bitdefender Total Security 2024
|

|
|
|